
There has been a fake copyright infringement takedown email claiming to be from an upset photographer or graphics designer going around the internet for the past few months. If you fall for the scam, it could result in your computer being infected with malware or ransomware.
As a website owner or blogger, we receive a lot of emails daily. Most of it is usually spam or general messages from our website’s visitors. When we get a copyright infringement notice, we tend to sit up and take notice since ignoring them could result in monetary penalties or the hosting service disabling your site.
Table of Contents
The Scam Copyright Email
I had received several emails submitted via the contact form for one of my WordPress sites claiming to be a copyright infringement takedown notice from a photographer with a link to a document listing the images in question.
Here is one of the emails is below:
Subject: Attention: www.XXXXXXXXX.com DMCA Copyright Violation Notification
Hello there!
My name is Marianne.
Your website or a website that your company hosts is violating the copyright protected images owned by myself.
Check out this official document with the links to my images you utilized at www.XXXXXXXXX.com and my earlier publications to obtain the evidence of my copyrights.
Download it now and check this out for yourself:
https://firebasestorage.googleapis.com/v0/b/[REDACTED]
I do think you have intentionally violated my rights under 17 U.S.C. Section 101 et seq. and could be liable for statutory damages of up to $110,000 as set forth in Sec. 504 (c) (2) of the Digital Millennium Copyright Act (”DMCA”) therein.
This message is official notification. I seek the removal of the infringing materials referenced above. Please take note as a service provider, the Digital Millennium Copyright Act requires you, to remove and/or deactivate access to the copyrighted content upon receipt of this particular notification letter. If you do not stop the utilization of the above mentioned copyrighted materials a legal action will likely be commenced against you.
I have a good faith belief that use of the copyrighted materials referenced above as presumably infringing is not authorized by the legal copyright owner, its legal agent, as well as law.
I declare, under consequence of perjury, that the information in this notification is accurate and that I am the copyright proprietor or am authorized to act on behalf of the owner of an exclusive and legal right that is allegedly violated.
Sincerely,
Marianne Wilkerson
Here is another email I got a month earlier:
Subject: You’re not allowed to use my images for www.XXXXXXXXX.com without my license! It’s illegitimate! You’re committing a legal offense! You must replace my images right now!!!!
Hello there!
This is Melia and I am a professional photographer.
I was baffled, frankly speaking, when I came across my images at your web-site. If you use a copyrighted image without an owner’s approval, you should be aware that you could be sued by the copyright holder.
It’s unlawful to use stolen images and it’s so disgusting!
See this document with the links to my images you used at www.XXXXXXXXX.com and my earlier publications to obtain the evidence of my ownership.
Download it now and check this out for yourself:
https://sites.google.com/view/[REDACTED]
If you don’t delete the images mentioned in the file above during the next couple of days, I’ll file a complaint on you to your hosting provider stating that my copyrights have been severely infringed and I am trying to protect my intellectual property.
And if it is not enough, you may be pretty damn sure I am going to take it to court! And I will not bother myself to let you know of it in advance.
Each email I received had a slightly different name of the photographer and a few words here or there modified. I think they do it to make it harder for people to Google to see if the takedown notice is legitimate.
Normally, spam and scam emails are pretty easy to spot due to poor grammar or spelling mistakes. I would say this one could be convincing enough to fool some unsuspecting site owners who are less tech-savvy.
Since I always use royalty-free photos from major stock photography sites, alarm bells started going off in my head.
Upon further scrutinizing the email, the scammer was trying to trick the victim into clicking a link to a file stored on Google Drive. This was another red flag. Usually, people will include the URLs to the images in question within the body of the email. A normal person will rarely take the extra trouble to list the images in a separate document and upload them somewhere else.
If you clicked the link, you will be asked to download a zip file that contains a javascript (.js) file.
When the javascript file is run through a virus scanner, it is reported as a Trojan downloader.
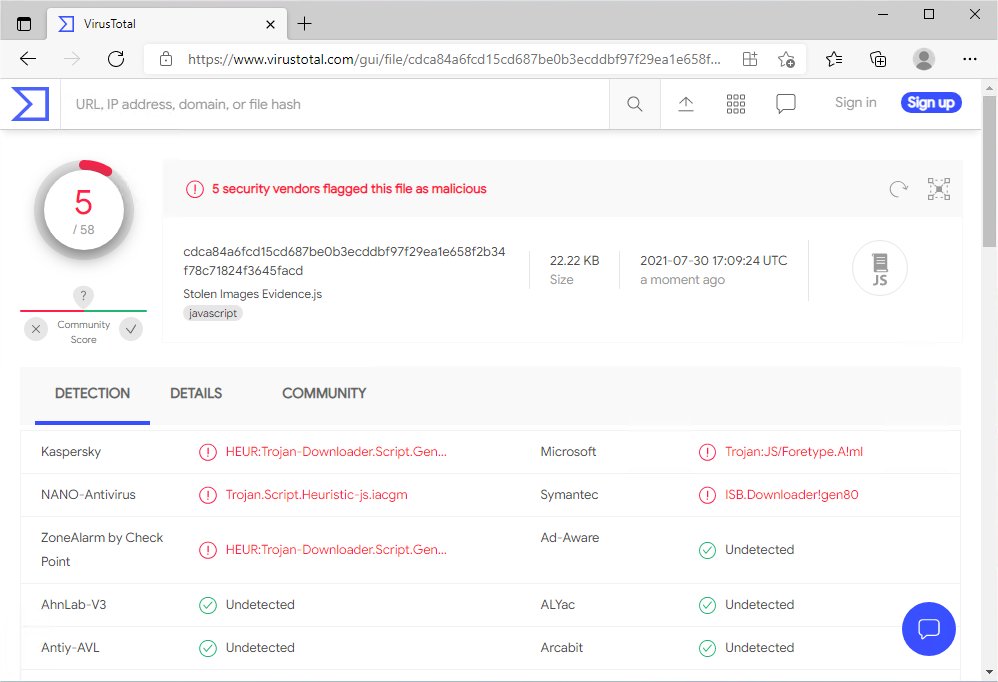
They may have been targeting website owners in hopes of getting access to their site’s web hosting, WordPress admin panel, or domain name through phishing attacks or installing backdoors, keyloggers, and other malware.
How to Protect Yourself from Hackers and Scammers
The general advice you often hear is to never click on links or download attachments from unknown sources. This is easier said than done.
Every person who visits your site or blog is someone you don’t know. I sometimes get commenters on the blog who add a URL with their comment. Unless I want to approve a comment and risk readers ending up on a sketchy site, I should know where the URLs are going.
Here is how I stay safe.
Install Antivirus Software
Antivirus software is your first line of defense against malware. Many antivirus programs now have real-time scanning that continuously scans your computer and websites to block viruses, malware, spyware, ransomware, and phishing attempts.
Here is a list of popular antivirus software:
| Antivirus Software | Platforms Supported |
| Avast | Windows, Mac, Android, iOS |
| AVG | Windows, Mac, Android, iOS |
| Bitdefender | Windows, Mac, Android, iOS |
| Kaspersky | Windows, Mac, Android, iOS |
| McAfee | Windows, Mac, Android, iOS |
| Malwarebytes | Windows, Chromebook, Android, iOS |
| Norton | Windows, Mac, Android, iOS |
| Trend Micro | Windows, Mac, Android, iOS |
| Webroot | Windows, Mac |
Use A Sandbox
A sandbox is a testing environment or virtual machine that allows you to run potentially unsafe software or visit suspicious websites without them affecting the rest of your computer. Once you are finished using the sandbox, you can close the program or shut down the virtual machine and everything inside will be wiped clean.
I used to install a fresh copy of Windows in a full virtual machine using Virtualbox. That turned out to be too much work and took too much time.
Today, I use Windows Sandbox. This feature is available if you are running Windows 10 Professional, Enterprise, and Education editions and on the May 2019 (19H1) update or later. Window Sandbox is not available on Windows 10 Home.
Windows Sandbox lets you quickly fire up a virtual copy of Windows as if you had just installed a fresh copy of Windows 10.
To enable Windows Sandbox, follow these steps:
Step One: Make Sure Virtualization is Enabled
You will need a CPU that supports virtualization. To check whether virtualization is supported by your computer, open up the Task Manager by pressing Ctrl + Shift + Esc. Then click on the Performance tab and look for “Virtualization: Enabled” under CPU.
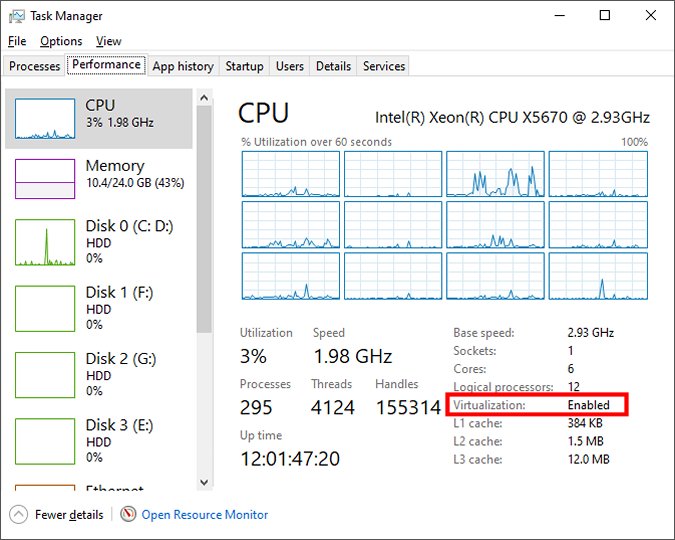
If it is not enabled, you will need to search online to see if your CPU has this feature and enable it in your BIOS if it is supported. Typically, all Intel processors after 2005 and AMD processors after 2006 should support virtualization.
Step Two: Enable Windows Sandbox Feature
To enable the Windows Sandbox, right-click on the Start button and click “Search”.
In the search box, type “Windows Features” and click on the “Turn Windows features on or off” in the result.
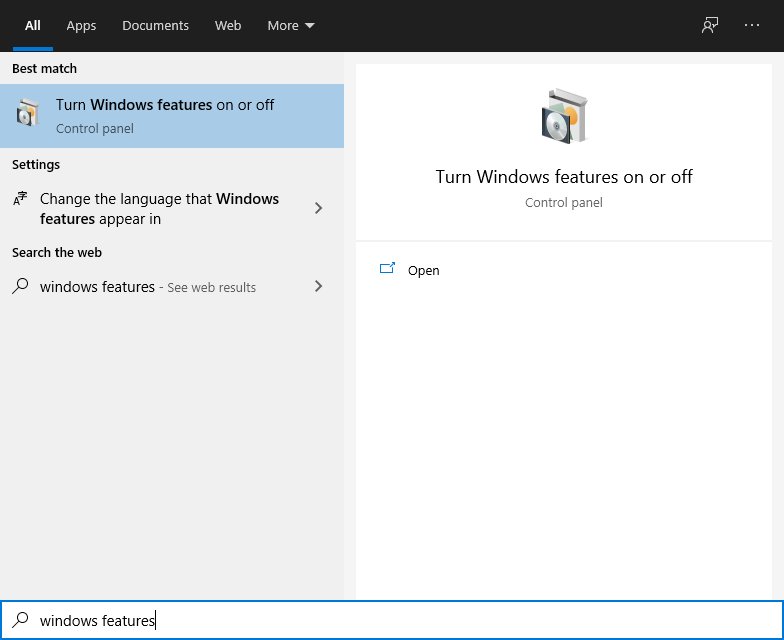
In the Windows Features window, click the checkbox to enable “Windows Sandbox” and click “OK”.
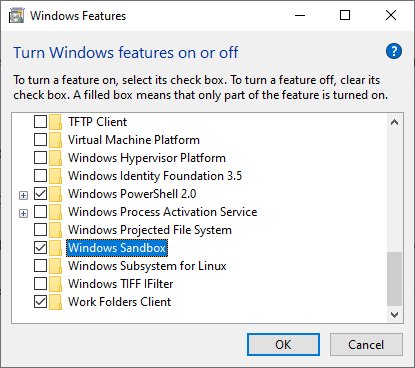
Windows will then ask to restart.
Step Three: Launch Windows Sandbox
After Window finishes rebooting, you can launch the Windows Sandbox by clicking on the program in the Start Menu or searching for “Windows Sandbox”.
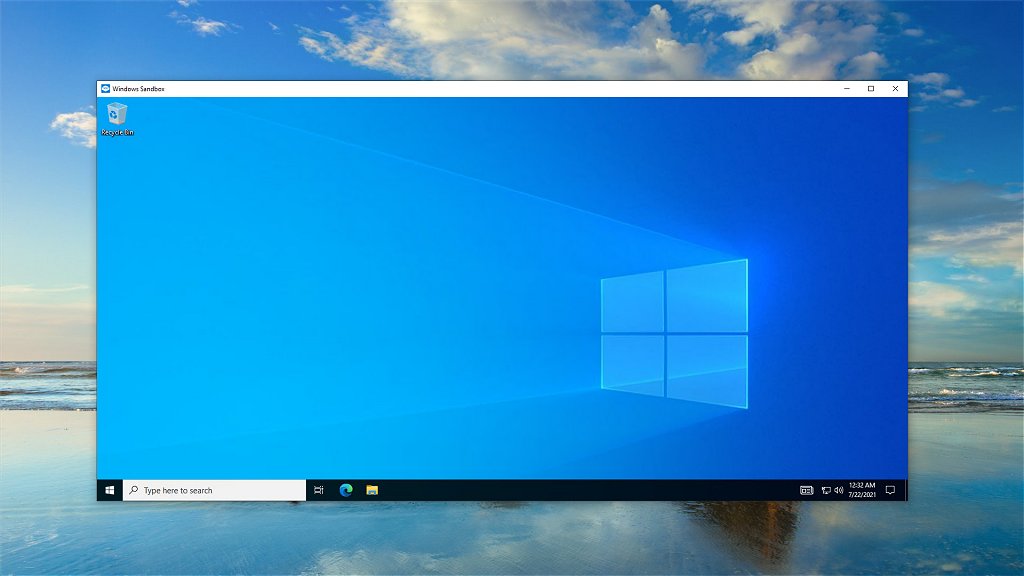
The newly launched Sandbox will have a copy of Microsoft Edge and Microsoft Defender Antivirus already installed. You may also be able to install your preferred antivirus software too as long as it doesn’t require a reboot. I was able to install and run Avast Antivirus successfully.
You can use copy and paste to put files in the Sandbox and then run them as you normally do. You can visit suspicious links with Microsoft Edge, and download questionable files all the while knowing everything in the Sandbox is quarantined from your main system.
Once you are done with your testing, close the Sandbox and everything within it will be destroyed.
Alternatives to Windows Sandbox
Those who are not running a copy of Windows that supports Windows Sandbox have a few other options.
You can install Sandboxie, an open-source sandbox application.
You can also run a virtual machine such as Virtualbox or VMware Workstation Player and install your own OS.
Submit Files for Online Virus Scanning
If you received a file and you are not sure if it is safe, you can download it (preferably within a sandbox) and then upload it to an online virus scanning tool such as Virus Total.
Virus Total will run it through over 70 antivirus and antimalware programs and let you know if it gets any hits.
Closing $ense
As a website owner or blogger, you are going to get many emails every day in your inbox. It gets even worst with bots spamming your website’s contact form.
Take a few extra seconds to assess the validity of any email message before blindly clicking on any links or downloading any attachments.
Besides running an antivirus program, a sandbox, or a virtual machine, you should keep your computer updated as Microsoft and Apple fixes any security vulnerabilities.
These tips will be useful even if you are not a webmaster or blogger. Lately, big companies, hospitals, and local government offices have been in the news from ransomware attacks that shut down their computer systems. It only takes one message and one person who is not careful.
Finally, never use images that you do not have the right to publish. While this instance of a photo owner claiming copyright infringement is a fake, using random images you find on Google is one of the major mistakes new bloggers make, and a mistake that could cost you a lot of money.
If you received a similar fake copyright infringement message, feel free to post it in the comments below after redacting any URLs and identifying information. This will help others who receive a similar email from falling for the trick if they do a Google search before downloading.
